Phishing emails target you to steal private information like your account details, login credentials and sometimes deceptively install harmful malware on your device.
Around 96% of phishing attacks are delivered using emails. Given such high numbers of attacks, it is imperative that you should be aware of such emails, what they look like, and how to deal with them.
This guide would cover all of these and talk about where you can report these emails if you got one.
Table of contents
- What is email phishing?
- What are the different types of email phishing?
- How to identify phishing emails?
- How to safeguard against phishing emails?
- Got a phishing email? Report it.
What is email phishing?
Email phishing is when attackers send malicious or fraudulent emails to scam the recipient and lure them into taking a specific action. Usually, phishing is a socially engineered act, where an attacker sends a deceptive email to psychologically manipulate the recipient to open the email and take action.
A phishing email can ask you to do any of the following:
Click on malicious attachments or links containing malware like ransomware.
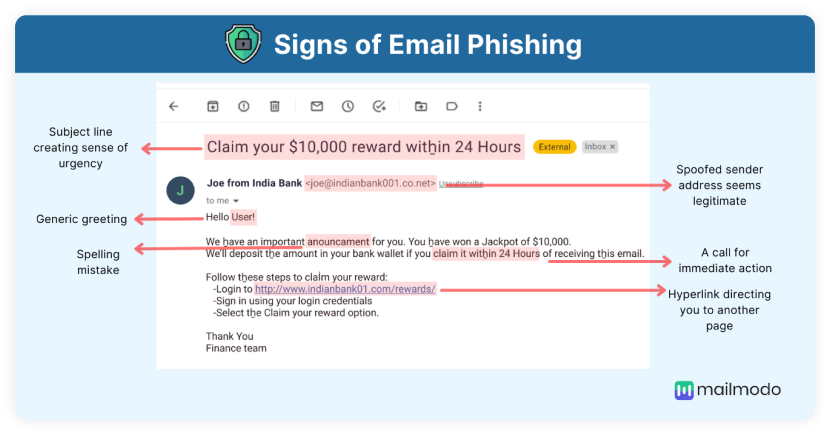
Click on an embedded link that redirects you to another page, likely a fake page. Such pages are designed to look legitimate to collect your information, such as login credentials or any other sensitive data.
Ask an employee, particularly those in the finance department, to transfer a big amount of money to some lookalike account.
What are the different types of email phishing?
Over the years, phishing has evolved from more than just credentials or data theft. The attacker’s intent behind phishing attacks can vary depending upon the type of phishing. There are broadly three kinds which are:
1. Spear phishing
Spear phishing involves sending emails to specific individuals, businesses, or organizations. Unlike generic phishing attacks, these emails are highly targeted, and the attacker spends time and resources researching the target and collecting information about the victim. As a result, they look legitimate and prompt the receiver to take action.
One kind of spear phishing is whaling, where attackers target high-profile people in the organization, especially the Chief Executive Officer (CEO) or Chief Operating Officer (COO).
2. CEO fraud
Under this phishing attack, the attacker sends emails to the employees, making it look like it has been sent by the CEO or any other high-profile executive. These phishing emails are mainly sent to ask employees to transfer money to some offshore account.
3. Clone phishing
Clone phishing is hard to detect as it is just a duplicate version of an email that the victim has already received. The only difference is that the cloned email contains malicious attachments and links sent from a spoofed email address, making it look like a legitimate sender has sent it.
So, phishing can occur in many ways, and recognizing them is crucial to protect yourself from such attacks. Let’s discuss how to recognize such emails.
How to identify phishing emails?
There are many ways you can spot phishing emails; some of them are as follows:
• Emails demanding urgent action
Phishing emails threaten to reveal any private information or cause loss of an opportunity unless you take the mentioned action. In that case, it’s a definite sign that email is a scam.
• Emails with bad grammar, spelling mistakes, or other typos
Phishing emails usually have grammatical errors and spelling mistakes as the attacker might not pay much attention to these things.
• Emails requesting your personal information, login credentials, etc.
Email from an authentic email address will never ask for your login credentials or other sensitive information.
If you get an email asking for such information, you should get cautious. Attackers make the email look legitimate and highly targeted, which might entice you to click the link and reveal sensitive information. So treat such email with caution.
• Suspicious attachments
Nowadays, most work-related attachments are shared via collaborative tools such as Dropbox, Google Drive, etc. If you find attachments or links that seem unfamiliar or suspicious, then chances are they are. Such attachments are often associated with malware like .zip, .exe, .scr, etc.
• Emails that seem too good to be true
Sometimes an email might ask you to click on a link claiming that you have won a lottery prize of work $10,000. Such emails are what we call too good to be true.
If the sender is unknown or you don’t recall buying any such lottery, you should refrain from clicking or engaging with the email.
• Emails with unfamiliar greetings or salutations
Email exchanges between colleagues or friends might be informal or contain words common to that conversation. If you see any unfamiliar greeting or salutation, then the chances are that email might be a scam.
Look at this phishing email example with different signs highlighted:
How to safeguard against phishing emails?
Due to increased work from home and virtual activities, phishing incidents have become widespread. That is why it is imperative to safeguard yourself against such attacks.
Here are the most effective ways to prevent phishing scams:
✅ Educate employees about phishing emails
Organizations can conduct security awareness training to educate employees about phishing and social engineering techniques. Sharing real phishing examples and steps to identify them can also help.
It is also imperative that everyone communicates and shares such incidents without fear or hesitation. Transparency and support can help foster a culture of cybersecurity and encourage every employee to be more vigilant of such emails.
One other good practice is to prioritize a phishing action on a complaint that seems genuine when you receive multiple phishing messages to better deal with them.
Related guide: Everything You Need To Know About Email Security
✅ Use Two-factor Authentication (2FA)
Two-factor Authentication is a reliable method for phishing protection. It adds an added layer of protection while you share sensitive personal information. As a result, 2FA can help mitigate the risk of revealing private information.
For instance, if you activate 2FA, then while paying money, you need to add your card details and OTP received on the registered mobile number. This way, you can think twice before making any transaction that seems suspicious.
✅ Don’t open or click on suspicious email links or attachments
If you think an email is phished, you should avoid clicking on any link or downloading attachments. Why? Because such malicious links or attachments can deploy the malware into your device, infecting or hacking your personal information.
✅ Install antivirus protection software on your devices
There are many antivirus software that offers real-time protection from phishing attacks. Such software helps you identify phishing emails, create unique passwords, protect your financial or other information from phishing scams.
Besides, if you received a phishing email and recognized it, you can report it.
Got a phishing email? Report it.
If you think you have got a phishing email, the first step is to report it to the right people. You should report it to your IT staff to review the email and take the required action on a corporate level.
On a general level, you can report phishing attempts to the Federal trade commission (FTC). They have a website dedicated to identifying theft and protecting you from future damages from such fraud emails. Besides that you should be aware about email security best practices to protect against email threats.


